On This Page: [hide]
Last month saw the start of a dangerous phishing scam aimed against WordPress site owners which is disguised as a DNS security upgrade email notification. The hackers are still actively using it as one of the main strategies to scam site administrators into falling into the scam. The final goal is to hijack their login data.
WordPress Site Owners Targeted By Large-Scale Email Phishing Scam: Impersonates a DNS Security Upgrade Notification
June 2020 saw the release of a large-scale email phishing campaign which targeted WordPress site administrators. This time the hackers have chosen to impersonate WordPress.com which is the managed hosting provider service that allows bloggers to easily set up their own site without having to use a dedicated web hosting company and setting up WordPress on their own. WordPress.com is preferred by many as it is operated by the same company who is behind the content management system.
These email messages are being sent in bulk by a hacking group that has designed the email notifications in order to look like legitimate messages. The criminal group behind the campaign is not known however given the fact that it is still operational shows that they have been able to reach a wide list of potential targets. The actual HTTP headers and information about the email senders can easily trick unaware website owners into thinking that the notifications are legitimate.
Also Read KingComposer WordPress Plugin Has a Reflected XSS Bug
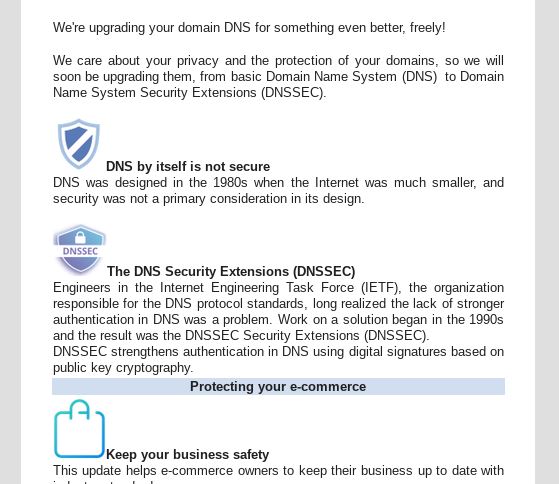
The criminals have hijacked logo images and design layout (page display, buttons and links) to appear as if they are come from the WordPress.com site. Given the fact that most similar email scams are involved with faking plugin or core system updates this one is designed to look like a DNS security update.
The message implies that the underlying DNS system used by the WordPress hosting service will migrate to the DNNSSEC – a strengthened DNS system which is based on the use of digital signatures based on the traditional public-key cryptography. The phishing email notification gives out a short description which sounds and looks authentic.
To complete the fake migration the recipients will be given a link to a phishing login landing page where they will be asked to enter in their credentials. If data is entered in these fields it will be automatically given to the hacker controllers.
Also Read How To Test Your WordPress Site Security
This WordPress phishing email campaign can be very succesful and dangerous due to the fact that the hackers can easily find out which blog is hosted on the WordPres.com managed hosting service and find out the contacts information of the owner. Against them the email can be customized with the necessary paarameters and the final notification will look like a real notification.
WordPress.com and generally all WordPress users can follow the basic security guidelines in order to protect themselves from falling victim to such phishing scams:
- Ignore Links Sent in Email Messages — Links that have been inserted in email messages claiming to be from an official service should be double checked if they lead to the official and legitimate domain.
- Use Two-Factor Authentication — This can mitigate most of the phishing scams as it introduces another form of login.
- Password Manager Recommended — Most security guidelines propose the use of password managers as they can generate and store strong passwords and keep them in a safe way. Most of them also include an URL guard.
- Anti-Virus Web Filtering — Many anti-virus products include live web filtering which includes an ever-updating blacklist of phishing sites.